Home > Software > libObfuscate Cryptography
libObfuscate
ISO C / open-source / system independent
Modern 256bit cryptography / scrambling
references and links (*)
How to:
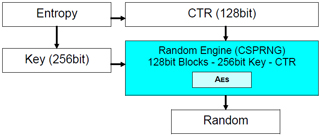
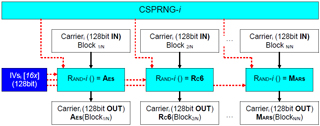
Link to your C projectCSPRNG - Based on AES:
Seed FunctionsHashing - 512bit:
Grostl Keccak SHA2 SkeinCryptography - 256bit - ECB - 128bit block:
AES Anubis Camellia Cast-256 Clefia FROG Hierocrypt3 Idea-NXT
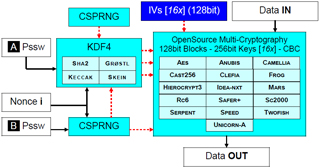
MARS RC6 Safer+ SC2000 Serpent Speed Twofish Unicorn-A WrapperMulti-cryptography:
256 + 256bit - CBC - Segment
How to: Link to your C project
|
CSPRNG - Based on AES: Seed
typedef enum {
|
|
HW AutoSeed : Seed = { Key , CTR } = RaceCondition ( )
CSPRNG_DATA csprng;
|
|
User interaction callback
// progress callback
|
CSPRNG - Based on AES: Functions
Functions
BYTE bValue = CSPRNG_get_byte( &csprng );
|
User interaction callbacks
// progress callback
|
Hashing - 512bit: Grostl
Hashing : hash [64] = Grostl ( inBuf [len] )
GROSTL512_DATA grostl;
|
Hashing - 512bit: Keccak
Hashing : hash [64] = Keccak ( inBuf [len] )
KECCAK512_DATA keccak;
|
Hashing - 512bit: SHA2
Hashing : hash [64] = SHA2 ( inBuf [len] )
SHA512_DATA sha;
|
Hashing - 512bit: Skein
Hashing : hash [64] = Skein ( inBuf [len] )
SKEIN512_DATA skein;
|
Cryptography - 256bit - ECB - 128bit block: AES
Encrypt : outBuf [16] = AES ECB ( inBuf [16] )
RIJNDAEL_STATIC_DATA rijndael;
|
Decrypt : outBuf [16] = AES ECB -1( inBuf [16] )
RIJNDAEL_STATIC_DATA rijndael;
|
Cryptography - 256bit - ECB - 128bit block: Anubis
Encrypt : outBuf [16] = Anubis ECB ( inBuf [16] )
ANUBIS_STATIC_DATA anubis;
|
Decrypt : outBuf [16] = Anubis ECB -1( inBuf [16] )
ANUBIS_STATIC_DATA anubis;
|
Cryptography - 256bit - ECB - 128bit block: Camellia
Encrypt : outBuf [16] = Camellia ECB ( inBuf [16] )
CAMELLIA_STATIC_DATA camellia;
|
Decrypt : outBuf [16] = Camellia ECB -1( inBuf [16] )
CAMELLIA_STATIC_DATA camellia;
|
Cryptography - 256bit - ECB - 128bit block: Cast-256
Encrypt : outBuf [16] = Cast-256 ECB ( inBuf [16] )
CAST256_STATIC_DATA cast256;
|
Decrypt : outBuf [16] = Cast-256 ECB -1( inBuf [16] )
CAST256_STATIC_DATA cast256;
|
Cryptography - 256bit - ECB - 128bit block: Clefia
Encrypt : outBuf [16] = Clefia ECB ( inBuf [16] )
CLEFIA_STATIC_DATA clefia;
|
Decrypt : outBuf [16] = Clefia ECB -1( inBuf [16] )
CLEFIA_STATIC_DATA clefia;
|
Cryptography - 256bit - ECB - 128bit block: FROG
Encrypt : outBuf [16] = FROG ECB ( inBuf [16] )
FROG_STATIC_DATA frog;
|
Decrypt : outBuf [16] = FROG ECB -1( inBuf [16] )
FROG_STATIC_DATA frog;
|
Cryptography - 256bit - ECB - 128bit block: Hierocrypt3
Encrypt : outBuf [16] = Hierocrypt3 ECB ( inBuf [16] )
HIEROCRYPT3_STATIC_DATA hierocrypt3;
|
Decrypt : outBuf [16] = Hierocrypt3 ECB -1( inBuf [16] )
HIEROCRYPT3_STATIC_DATA hierocrypt3;
|
Cryptography - 256bit - ECB - 128bit block: Idea-NXT
Encrypt : outBuf [16] = Idea-NXT ECB ( inBuf [16] )
IDEANXT128_STATIC_DATA ideanxt;
|
Decrypt : outBuf [16] = Idea-NXT ECB -1( inBuf [16] )
IDEANXT128_STATIC_DATA ideanxt;
|
Cryptography - 256bit - ECB - 128bit block: MARS
Encrypt : outBuf [16] = MARS ECB ( inBuf [16] )
MARS_STATIC_DATA mars;
|
Decrypt : outBuf [16] = MARS ECB -1( inBuf [16] )
MARS_STATIC_DATA mars;
|
Cryptography - 256bit - ECB - 128bit block: RC6
Encrypt : outBuf [16] = RC6 ECB ( inBuf [16] )
RC6_STATIC_DATA rc6;
|
Decrypt : outBuf [16] = RC6 ECB -1( inBuf [16] )
RC6_STATIC_DATA rc6;
|
Cryptography - 256bit - ECB - 128bit block: Safer+
Encrypt : outBuf [16] = Safer+ ECB ( inBuf [16] )
SAFERP_STATIC_DATA saferp;
|
Decrypt : outBuf [16] = Safer+ ECB -1( inBuf [16] )
SAFERP_STATIC_DATA saferp;
|
Cryptography - 256bit - ECB - 128bit block: SC2000
Encrypt : outBuf [16] = SC2000 ECB ( inBuf [16] )
SC2000_STATIC_DATA sc2000;
|
Decrypt : outBuf [16] = SC2000 ECB -1( inBuf [16] )
SC2000_STATIC_DATA sc2000;
|
Cryptography - 256bit - ECB - 128bit block: Serpent
Encrypt : outBuf [16] = Serpent ECB ( inBuf [16] )
SERPENT_STATIC_DATA serpent;
|
Decrypt : outBuf [16] = Serpent ECB -1( inBuf [16] )
SERPENT_STATIC_DATA serpent;
|
Cryptography - 256bit - ECB - 128bit block: Speed
Encrypt : outBuf [16] = Speed ECB ( inBuf [16] )
SPEED_STATIC_DATA speed;
|
Decrypt : outBuf [16] = Speed ECB -1( inBuf [16] )
SPEED_STATIC_DATA speed;
|
Cryptography - 256bit - ECB - 128bit block: Twofish
Encrypt : outBuf [16] = Twofish ECB ( inBuf [16] )
TWOFISH_STATIC_DATA twofish;
|
Decrypt : outBuf [16] = Twofish ECB -1( inBuf [16] )
TWOFISH_STATIC_DATA twofish;
|
Cryptography - 256bit - ECB - 128bit block: Unicorn-A
Encrypt : outBuf [16] = Unicorn-A ECB ( inBuf [16] )
UNICORNA_STATIC_DATA unicorn;
|
Decrypt : outBuf [16] = Unicorn-A ECB -1( inBuf [16] )
UNICORNA_STATIC_DATA unicorn;
|
Cryptography - 256bit - ECB - 128bit block: Wrapper
Encrypt : outBuf [16] = Cipher ECB ( inBuf [16] )
MULTI_STATIC_DATA multi;
|
typedef enum {
|
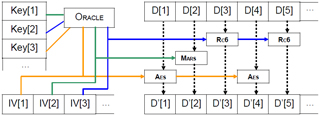
Multi-cryptography - 256 + 256bit - CBC - Segment
Encrypt : buf ' [k * 16] = Multi-cipher CBC ( buf [k * 16] )
MULTI_DATA multi;
|
|
Decrypt : buf [k * 16] = Multi-cipher CBC -1( buf ' [k * 16] )
MULTI_DATA multi;
|
|
User interaction callbacks
// progress callback
|
 Download (source & redistributable Windows DLL)
Download (source & redistributable Windows DLL) Manual
Manual libObfuscate on SourceForge
libObfuscate on SourceForge